Reference :
- Network Attacks and Exploitation by Matthew Monte
- The Australian National University CECS
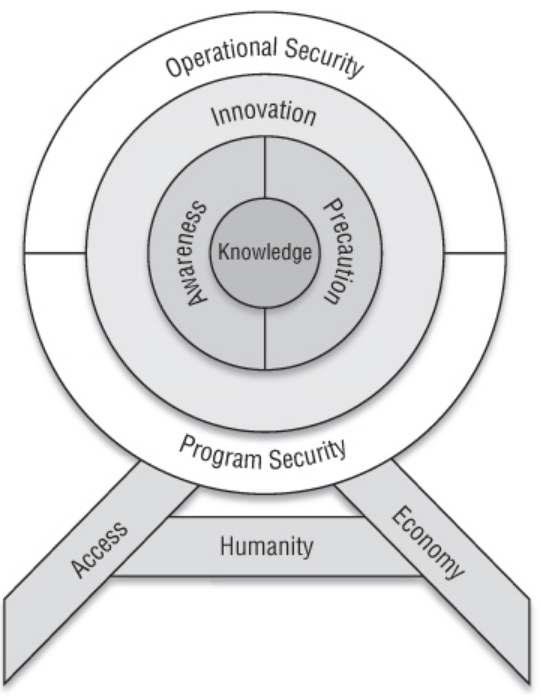
Target
Five levels of target: Operation Scope —> Networks —> Subnet/VLAN —> Systems —> Software.
Five influential elements:
- Launch Points: Where can this target point be engaged from?
- Cover: 누구로 위장? 네트워크를 뚫고 침입해서 정보를 뺴갈만한 사람이 누구인가?
- Obstacles: 목표를 향하는데 방해/고려 요소들. 방어 체계가 어떻게 되어있나
- Key Terrain: 타겟에 접근하기 전에 해두어야 (이뤄두어야 할) 요소들
- Gaps: 목표의 첫 진입로는 무엇인가
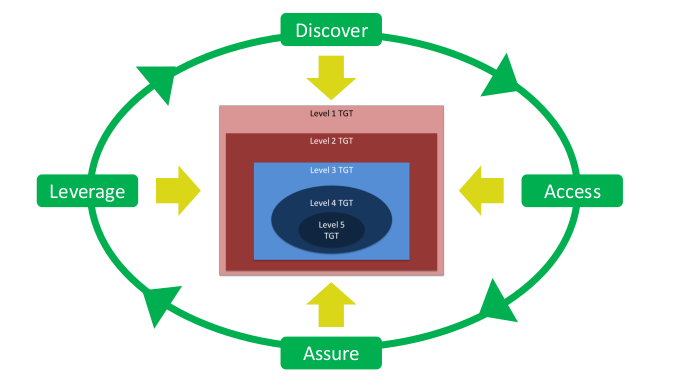
위 네가지 요소들은 시작전에도 필요하지만 작전이 진행되면서 계속해서 바뀌어간다.
Tactics
Discovery
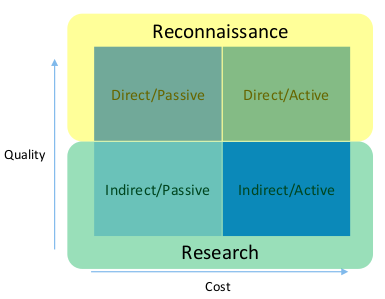
has Two Modes:
- Passive: no negative effect on the target
- Active: Provoking a system to observe its response
has Two Vectors:
- Indircet: Interacting with infrastructure not controlled by the target
- Direct: Engaging target infrastructure
Research: 타겟에 대한 정보를 직접적인 건드림 없이 모으는 행위.
- 리서치의 목표는 정찰 활동에 집중하기 위해서
- 호스트 발견하기 위해서
- 작전 보안의 위험성을 낮추기 위해서
- 정보는 미완성이고 관련성과 최신성이 낮다
- 존재하는 정보들을 모으는 단계라고도 볼 수 있는데 두가지가 있음
- Harvesting: 목표와 관계된 정보들을 최대한 모아서 그곳에서 목표 가능한 개체를 찾는것
- 웹사이트 컨텐츠나 서류에서 정보를 수확할 수 잇다
- 인터넷 인프라 - 지역 인터넷 이용자, DNS등
- 컨텐트와 메타데이터 로부터 얻는 이메일과 이름, 아이피 주소와 도메인등
- Mining: 하나의 개체를 중심으로 정보를 더 깊게 파는행위
- 구글 크롤링이나 인덱스
- 제 3자 정보 모아주는 서비스 이용 (무료/유료)
- Google, Shodan, Maltego
- Harvesting: 목표와 관계된 정보들을 최대한 모아서 그곳에서 목표 가능한 개체를 찾는것
Reconnaissance: 리서치 단계로부터 얻는 결과에 대한 확인과 보완 작업
목표는 물리적 시스템과 소프트웨어
목표와 직접적으로 반하기 때문에 들킬 수 있다.
가장 최신화된 정보를 제공함
타겟에 대한 접근성을 테스트 함
좀더 현실성 있는 정보들을 흭득하는데 두가지 방법이 있음
Scanning: 사이버 레이더와 비슷함
- 호스트, 서비스, 버전등의 발견을 목표로함
- Port scanning, Service enumeration, Ping. Trace Route, Firewalking, DNS zone transfer 등
Probing: 목표를 도발(건드림) 함으로써 반응을 살핀후, 치명적인 약점을 찾아내는것
- 훨씬 시끄럽고, IDS/IPS signatures 로 부터 수상한 움직임으로 발견될 수 있음
- 목표 시스템을 심문함으로써 취약점을 발견
- Vulnerability scannig, fuzzing, brute forcing, stress testing.
Password
해쉬는 디스크 혹은 확인 절차중의 트래픽에서 수집된다
트래픽에서 하는 해쉬가 훨씬더 보호되고 풀기도 어렵다
해쉬를 크랙킹 하는것은 오프라인 공격에 해당된다
온라인 공격은 시스템이라 웹사이트 로그인 기능에 대한것이다
보통 브루트 포스와 딕셔너리 (해쉬 저장된)를 이용한다.

Access
보통 해킹이라 불리는 단계가 이 단계
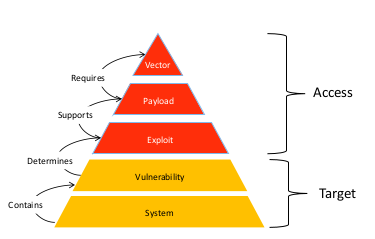
- Exploit: 소프트웨어 취약점을 목표로 한 코드. 목표 시스템에 들어가서 payload 를 실행함
- 두 시스템간의 신용 (trust)을 이용함
- 백엔드의 경우 프론트엔드를 믿고 받은 커맨드를 실행함. 따라서 프론트엔드의 실수가 백엔드로 이어지는것 (트위터 포스트에 코드 올려서 인풋이 실행된다던가 혹은 SQL Injection)
- 혹은 중간에 들어가서 클라이언트, 서버 역할을 해서 정보를 뺴낸다던가
- Payload: 목표 시스템에서 해커에게 access 제공하는 코드
- 해커에게 문열어주기, 더 많은 페이로드 설치하기 (한번에 다 보내면 위험하니까), 셋팅 바꾸기 (그리고 사라짐)
- Vector: 시스템 공격부터 목표까지 도달하기 위한 위 두가지를 전달하기 위한 이벤트의 절차나 순서들
- 직접 (해커-목표), interception (정당한 다른 시스템-목표 평소 사용하던 광고 사이트에 광고 요구, 광고가 감염됨 (서버아님) — watering hole attack), redirection (목표를 위험한 사이트로 인도하는것 - 서버가 감염됨))
Assure (확실)
- 접근은 작전의 시작 부분이고, 이 확실 부분이 접근과 실행단계를 연결해주는 다리 역할
- 이 확실 단계가 가장 들키기 쉬운 단계로 다른 부분들에 비해 제일 위험하다
- 접근은 너를 문안으로 발자국을 딛게 해주고, 확실은 문 키를 주는것.
- 작전에 따라 확실 정도가 달라짐
- 작전 완료를 위한 시간 버는 중요한 단계
- 결과론적으로 확실단계는 작업 필요성과 타겟과의 마찰을 적절하게 유지하는 것.
접근과 마찬가지로 시스템, 네트워크 레벨 총 두단계로 나눠지는데
- System Level Assurance: 특정한 시스템에 접근권한을 유지하는것
- Network Level Assurance: 네트워크에 접근권한을 유지하는것. 네트워크 레벨 접근은 사실 시스템 접근성에 기반을 두고 있다.
접근의 경우 방어나, 혹은 자연적인 시스템에 의해 잃을수 있다.
Access Losing action 은 사람이나, 기계의 방해에 따른 (방어나, 혹은 중립적인 시스템 이벤트에) 결과이다.
Hostile: 너의 칩입을 겨냥한 반응
Neutral: 자연적인 시스템 사건에 의한 반응
Human: 사람의 선택에 따른 반응 (업데이트/업그레이드 혹은 설정 바꾸기등)
Machine: 머신의 프로그래밍에 의한 반응
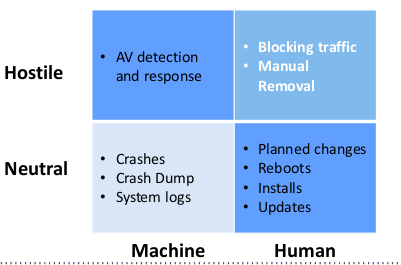
Assurance - Sub-components
Security
상대방의 행동으로 인한 접근권한 잃는것을 지켜준다.
접근 보안이 Assurance의 세 부분중 (보안, 감시, 잠행) 가장 먼저 지켜져야 한다
보안은 redundancy를 통해 (즉 백도어) 달성될 수 있다.
백도어의 중요한 원칙은 백도어간의 단절화가 지켜져야 한다.
백도어는 두가지 방법으로 설치가 가능한데
- 타겟 시스템에 새로운 소프트웨어를 설치하는법
- 타겟 시스템에 존재하는 소프트웨어를 수정하는법
Redundancy는 한 접근 방법을 잃을 때 다른 접근 방법이 남겨지는것이다.
접근 위험을 퍼트려야 한다 (하나 걸릴때 다른거 안걸리게)
첫번째 접근 했던 방법을 고려해서 이 방법에 영향 받지 않는 두번째 접근 방법을 고려해라.
복제 형식으로도 가능하지만, 이는 곳 signatrue를 강하게 남긴다는 뜻이다
완벽한 단절은 엄청난 시간과 투자를 요구한다.
보안의 목적은
수화물이 프로세스가 죽었을때 다시 켜지는것
공격 스테이션이 실행되고 있는 수화물에 접근 가능하게 하기 위해 (즉 프로그램 심어놓고, 그 프로그램에 대한 접근이 가능해야 뭘 하지)
보통 두가지를 사용하는데
Bootstrapping : 수화물을 운영체제에 연결하는법
- 윈도우의 경우, 시작폴더, 서비스, 레지스트리 들을 참조한다
- 스케쥴링은 어플리케이션 실행하는데 다른 방법이다.
Beaconing: 타켓에서 공격자 인프라에 연결을 하게 하는것.
- 접근 세션 혹은 정보의 변경/추출 을 시도한다.
- 정기적으로 beacon에 의해 수화물이 설정변경 가능하다 (타겟이랑 연결되어 있으니 수화물 조정이 가능하지)
- 해당 시스템의 운영체제에 있는 어플리케이션이나, 새로 다운된 것들을 실행하도록 스케쥴링을 시킬수 있다.
Surveillance
위험성을 감지함으로써 적절한 반응 (responsive action)을 시간내에 가능하게 해준다
Is only an enabler to responsive action or investigation.
May alert to threatening actions and allow you to take timely action.
접근을 잃으면 이 감시를 더 분석하고, 미래의 접근 방법을 조정하게 해준다
시스템/사람 모두로 인해 위협이 일어나니 모두 고려해야한다
감시 기간동안 걸리면 접근이 차단될 수 있다. (즉 감시 하다가 걸리면 당연히 뭘 하겠지 상대방이)
로컬 atcivity 들을 모니터링 함으로써 시스템의 위협을 감지 할 수 있다.
그 행동이 (activity) 가 중립적인지 적대적인지를 확인하는것이 시스템 위협 모니터링의 목적이다
보통 적대적 시스템 행동은 보안 기기나 보안 소프트웨어에 의한다
목표 기기가 알아차린것과 사람이 반응하는 시간 차이는 목표물의 보안 성숙도와 교양에 달려있다.
사람 위협의 감지는 기기와 인간이 만든 컨텐트들의 모니터링을 필요로 한다
사람 행동을 로컬 시스템 이벤트들로 감지 가능하다
사람이 만든 컨텐트는 잠재 위협 행동의 가장 좋은 지표이다 (사람이 뭘 만들었으면 시스템이 바뀔 예정이니 뭐가 어찌될지 예상/확인이 가능하다)
이러한 감시들은 관리자 워크스테이션에서 존재해야 가능 할 수 있다 (may)
Assurance는 관리자 시스템에 접근하기 위함이 첫번째 이유이다.
모니터링에는 두가지 종류가 존재하는데
Static Monitoring: take a snap of target activity (processes, stats, logs).
- 커맨드를 사용해 파일로 만들고, 압축해서 보낸다. 부트스트래핑을 이용한 방법이다.
Dynamic Monitoring (Real time): 특정 행동들을 감시하는것
- 저장하고, 쿼리로 만들고, 테스트를 하고, 필요한 정보가 있다 하면 보내는것 아니면 폐기.
Stealth
Assure 단계에서 가장 마지막에 고려되며, 초기 접근과 Assurance 활동의 들킴을 방지한다
잠행은 공격적/방어적 인 방법이 있는데, 방어적은 은엄폐를 통해서, 공격적은 상대방의 센서능력의 하락을 통해서 이루어진다
방어적 장행
위장과 엄폐를 사용한다
엄폐는 감시 능력 밖에 위치하거나, 들킬만한 것들을 제외 함으로써 가능하고
위장은 들키더라고 안걸리고 넘어가는것
타켓 네트워크와 시스템이 자연적 위장을 가능하게 해준다 (즉 그 상황을 사용)
공격적 잠행
최후의 보루로, 높은 위험성을 내포하지만 같은 결과를 도출함 (즉 걸리지만 않으면 좋음)
상대방 감지 능력 감소를 야기함
감지를 직접적으로 공격하거나, 간접적으로 공격함
직접적인 방법은 disablement or reconfiguration
간접적인 방법은 chaff - deploying more observable to attract (즉 함정 쓰는거) 디코이
Assurance를 디자인 하는것인 작전 결정이며 목표와 키 위험성을 고려해야한다
- 다른 단계에 비해 가장 높은 위험성을 내포하고 있고 (위험 메니지먼트에 가장 크게 의존함)
- 두가지 성질에 의해 measure 가능하다
- Operational Equities: Customer owned. Wider investment in operational
outcomes. Affects stakeholders. - Capability Equities: Internally owned. Investment in infrastructure, tools and
tradecraft.
- Operational Equities: Customer owned. Wider investment in operational
단계별 관계도
- Resilence (복원력) 는 모니터링의 요구도를 줄일 수 있다. 하지만 모든 Resilence 메카니즘이 모니터되는건 아님 (즉 요구도를 줄이지만 없애지는 못함)
- 좋은 모니터링과 반응은 light resilence를 커버할 수 있다. 하지만 모니터링은 alert to resilence mechanisms 할수 있다
- 모니터링 행동은 잠행 기회들을 발견 할 수 있다, 하지만 모니터링은 타겟 시스템에서의 활동을 늘린다
- 잠행은 발견 확률과 모니터링 요구도를 줄일수 있다. 하지만 잠행을 늘리는것은 모니터링의 감소를 필요로 한다 (시간은 유하니까)
- 발견 안되면 지우지 못함 (내가 있는지 모르니까), 하지만 이러한 잠행 기술들은 표식을 남긴다
- 내 활동들이 중간에 방해되지 않으면, 잠행을 덜 필요로 한다. 하지만 resilence의 증가는 시스템 활동을 늘리고 잠행을 줄인다.
Leverage : activities achieving operational objectives
Pillage (약탈하다) 상대방의 시스템에 접속해 정보를 약탈하는게 우선순위.
다른 감염된 호스트들 (감염시킨) 을 통한 pivoting 을 하여 접근한다.
약탈을 하는 목적에는 두가지가 있는데
- 관련된 요구 지식을 충족하기 위해서
- 네트워크와 시스템 접근과 assurance를 가능하기 위해서.
- 네트워크는 보통 라우터에 의한 서브넷, 그리고 스위치에 의한 가상랜으로 나뉘어져있다.
- 그 네트워크의 단절성을 통과하기 위해 피벗팅이 필요 할 수 있다.
- 한 시스템은 여러 가상랜위에 존재 할 수 있다 (회사 백엔드, 혹은 관리자 시스템) - 즉 가상랜을 통해 시스템 접근가능
Pillage
- 복사: 보통 유저 라이브러리, 로그, 비밀번호 해쉬등을 복사하며, 이 정보를 빼내기 위한 exfiltration 방법은 FTP, SCP, Netcat등 세션에 달려있다.
- 쿼리: 호스트나 해당 네트워크에 관한 정보를 생성함. 시스템에 특정 질문을 해서 (command) 관련 정보를 빼내는방법. 보통 > >> 같은 명령어로 txt 파일로 옴겨서 추출함
- 캡쳐링: 컴퓨터에 저장되지 않는 동적인 정보들을 캡쳐하는것. 서류 스크린샷, 키로깅, 네트워크 스니핑 (오고가는 데이터들 중간에 가로채는것 - 사이트/시스템 비밀번호 같은것들 포함)
Pivot
- Proxy: 클라이언트와 서버 사이에서 데이터를 전달해 주는 서버. 프록시는 패킷을 전달 받고 목적지에 전달해준다. 즉 다른 네트워크로 가는 게이트웨이 역할. 여러 프록시들이 모여서 프록시 체인을 형성하기도 한다.
- Tunnel: 프록시보다 더 복잡하다. 특정한 어플리케이션 트래픽을 만들어 내기위한 고급 방법. 터널링은 복잡한 트래픽 흐름을 만들수 있도록 조정가능하다. 한 희생양을 이용해서 목표물에 접근하는 방법.
- Shovel: 다음 작전을 위해 감염시킨 타겟에 도구들을 옮기는것. 즉 1번 타겟을 공격해서 감염시키고, 1번타겟에 도구들을 올려서 타겟 2를 공격하는것. 즉 나는 명령어를 1에 내리면 1이 2를 공격하는것. 타겟에 도구를 옮겨야 하는만큼 들킬 가능성이 높다, 대신 연결 실패할 확률이 적음 (연결 실패 확률이 적은 컴퓨터를 감염시키겠지)