
Reference : Network Attacks and Exploitation by Matthew Monte
Crafting a successful strategy requires:
- A clearly defined goal; strategic collection, directed collection, non-kinetic CNA, strategic access and positional access.
- Embracing the fundamental truths of the space; three foundational principles: humanity, access, and econmoy.
- Determining and reducing the uncertainty of frictions while increasing the opponent’s.
- Determining and maximising advantageous asymmetries, while minimising the opponent’s.
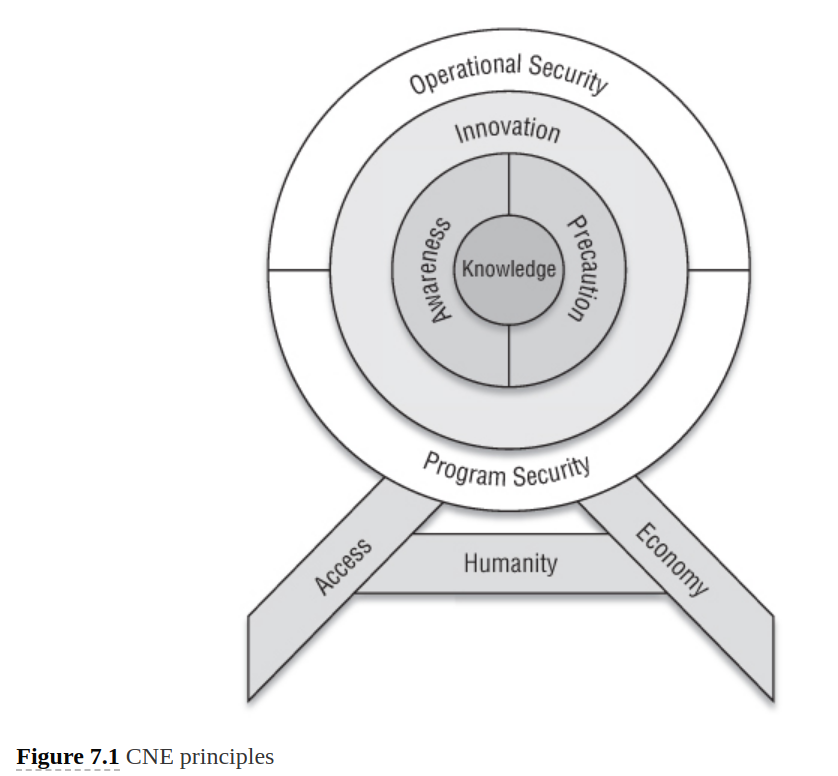
Principle 1: Knowledge
- Is the in-depth understanding of the tech aspects of architecture, OS, Network, and so on as well as psychological aspects of people and organisation.
- Is the target agnostic and acquired outside of any specific operation.
- Is essential to leverage all three principles: access, humanity, economy.
- Reduces frictions - helps reduce flawed attack tool.
- It costs time and money
- Has limits of incompleteness and inaccuracy.
The best decisions are made by those that have a balance of knowledge of the thech, psychological, and social aspects of operations
Principle 2: Awareness
- Is the careful mapping of the operational domain as well as the active detection and passive monitoring of events in near real time.
- Is gleaned from the target environment and is target specific.
- Seeks to counteract the Defender’s asymmetrical advantage of turf control.
- May allow the attacker to discern when the frictions of updates and upgrades are coming where they will be deployed.
- May tell the attacker the likelihood and consequences of being caught - as can see hows the security going by humans aspects.
- Leads to the more effective deployment of tactics - as aware of the ongoing situation.
- Requires greater exposure and risk - need expansion to collect awareness.
- Too much —> may lead overconfidence or can be paralysing (too much worries).
- Buys time: to innovate, to put in redundancy, to collect data, and clean up and out.
Principle 3: Innovation
- Is the ability to create new technology, leverage existing technologies in new ways, or develop and adapt operational methods.
- Requires creativity; essential for finding flaws by divining assumptions that engineers and administrators may have not realised they were breaking.
- Is creativity brought to scale through sound engineering.
- Can improve efficiencies and decrease frictions.
- Confers a tactical advantage.
Principle 4: Precaution
Consider the effects of the Defender’s actions on the Attacker
- Is the minimisation of the effect of unwitting (자신도 모르는) actions on an operation.
- Is the strategic principle that fills the void left by the impossibility of obtaining total awareness.
- Redundancy: is establishing reasonable fail-safes, backups, and contingency methodes, network signatures.. - allows the operation lives
- Diversity: is leveraging a wide range of tools, technologies, development methods, network signatures… - prevent full operation failure.
- Redundancy - Points of acceess per seg = lg(number of devices)
- Diversity = 1 to 2 methods / platform.
- The best precaution will depend on the attacker’s level of awareness.
Principle 5: Operational Security
Consider the impact of the Attacker on the Defender.
- Is the minimization of adversarial exposure, recognition, and reaction to the existence of an operation.
- Is best defined as doing everything that prevents discovery.
- Is the twin of the principle of precaution; Precaution - the effects of the Defender’s actions on the Attacker, Operational Secu - the impact of the Attacker on the Defender.
Minimizing Exposure
- Stealthness - more than active hiding; includes being a tree in a forest.
Minimizing Recognition
- Has level of exposure to observations.
- Ensure that observable artifacts and actions are kept within an expected pattern. (behave the common pattern they do)
- Decoy - spread out anomalous actions in space and time to keep below the human thrushold of perceived cause.
Controlling Reaction
- May leave decoys that misdirect Defenders into thinking they have rooted out the problem.
Measuring
The more awareness you have, the more secure you can be. But the act of acquiring that awareness is less operationally secure.
Principle 6: Program Security
- Is the principle of containing damage caused during the compromise of an operation.
- You do not want to affect the other operation from the failure of one.
Attacker Liabilities
- Anything that can be used to impede the Atttacker’s future operations.
- Defenders will do Battle Damage Assessment (BDA) - What
- What systems were compromised? What credit cards were exposed?
- What user accounts? What is the value?
- Defining who and how is intensive work.
- Categories are:
- Identity, Target Pollution, Attacker Infrastructure
- Technical Vulnerabilities, technical tools, Operational Methodologies.
Program Security Costs
Attacker Costs < Defender Costs is ideal.
Do following to increase the costs for defenders:
- AntiReverse Engineering - Prevent Static Analyze; Reverse Engineering - no control, but analyze and knows how does it work.
- AntiDebugging - Prevent Dynamic Analyze; Debugging - analyze with the control.
- Capability Diffusion: separate big into small segements so hard to define the links in between the programs.
— Careless increase of Defender’s analysis cost may trigger the detection and lose the superiority; with potential of decreasing the costs for them + decrease program security
- Mitigation is the cost of preventing the attacker’s actions in the first place, or cleaning up after successful attack detection. - 예방및 공격감지후 보호/정리 비용
- Distribution is the cost associated with either acquiring that knowledge or sharing with others : Computer Emergency Response Teams (CERTs)


