
Reference : Network Attacks and Exploitation by Matthew Monte
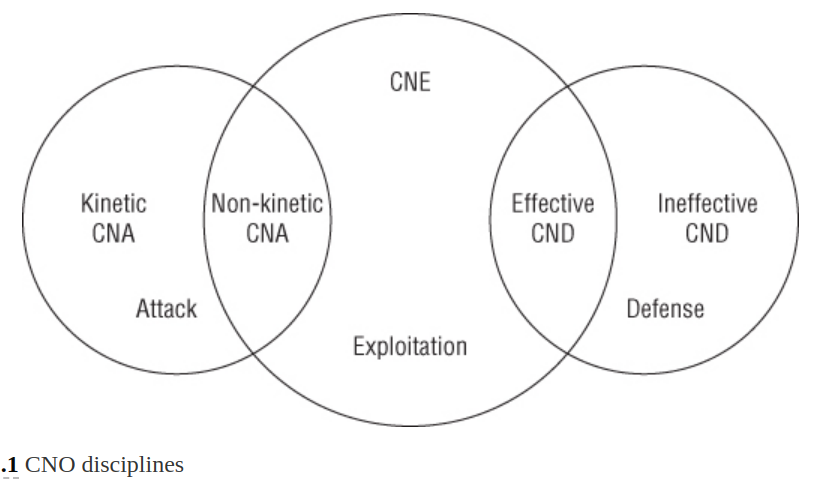
Computer Network Exploitation - CNE
- Is computer espionage; stealing of information.
- Encompases gaining access and retriev data.
- It is directed. If the action was from no intent to gather information, it is not CNE.
Comupter Network Attack - CNA
- Is akin to a traditional military attack or sabotage.
- Four Ds: disrupt, deny, degrade, destroy (회방, 방해, 효율 떨어트리기, 파괴)
- Actions and effects that range from the subtle to the catastrophic.
Non-kinetic CNA
- Subset of CNA conducted virtually; 4Ds virtually.
- Not physically initiated acts.
Computer Network Defense (CND)
- Protecting networks from being exploited or attacked.
Computer Network Operation (CNO)
- Is umbrella term of CNE, CNA , and CND.
Operational Objectives
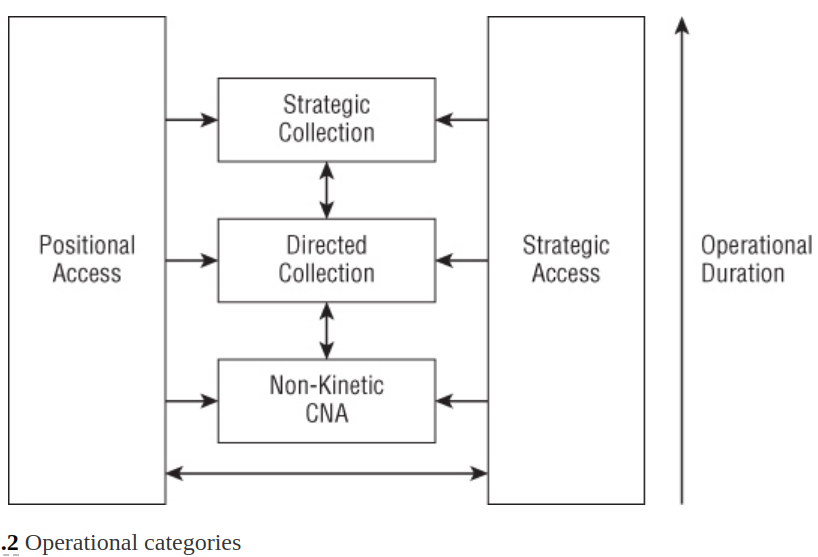
Strategic Collection
- Collecting information for strategic reasons.
- Collection of data over time.
- Requires substantial analytic capabilities for success due to the collected information size.
- The cost is huge, often limited to nation-states or well-funded criminals.
Directed Collection
- Target the collection of information to meet an immediate objective.
- Initial intend of the operation is known from the beginning.
- It may start with short life expectancy, but successful operations will be extended over time.
Non-Kinetic CNA
- Meant to Disrupt, Deny, Degrade, Destroy the operational capability of Computer Network.
- The information is leveraged to cause the damage rather than gathering information like the two aboves.
Strategic Access
- Executed for the purpose of future flexibility
- Unlike strategic collection, it hopes one day the access becomes useful.
- It may be led to other operational categories, or do nothing; nothing defined yet.
Positional Access
- target computers and network that are not the targets but useful to furthering a different objective.
- It may begin with a intent and expect short life, however may be extended like directed collection.
- If it is exetended, it carries the most risk as it may link other operations once detected.
CNE Framework
First Principles
Humanity
- Human Nature. Don’t forget it is the human who deals with.
Access
- There is always someone with the access. It exists for someone who has the access of it
Economy
- Priority, cost and benefit to every action and to every outcome — Money driven.
Principles
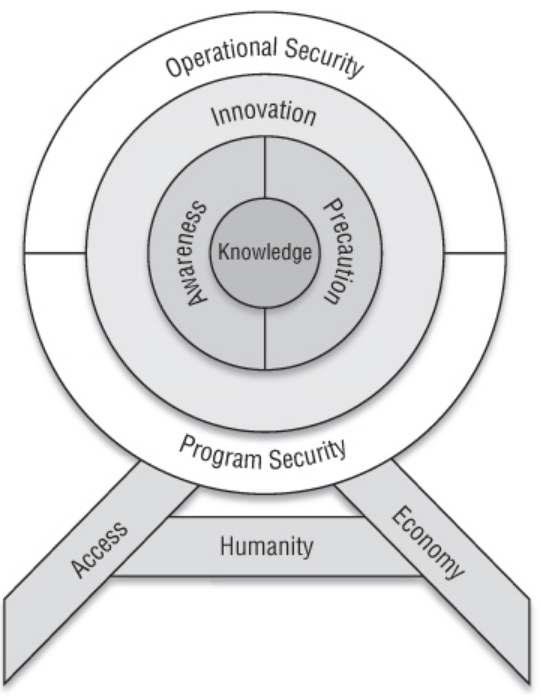
Knowledge
- Broad and deep understandingy of computers, network and behavioral and psychologicas characteristics of people and organization.
Awareness
- Mapping of the operational domain, including active detection, monitoring of events in near time (updates…)
Innovation
- Ability to create new technology, leveraging existing technologies, or develop and adapt operational methods to new circumstances.
Precaution
- Minimization of the impact of unwitting actions on an operation.
Operational Security
- Minimization of defender exposure, recognition, and reaction to the existence of an operation.
Program Security
- Containment of damage caused by the compromise of an operation.
Themes
Diversity
- Leveraging a wide range of tool, tech, development methods, network sig, infra, and operational methods…
Stealth
- Leveraging tools, tech, and methods that are hidden from view or unlikely attract attention.
Redundancy
- Reasonable fail-safes, backups, and contingency plans for foreseeable setbacks, and obstacles.
Themes must be considered within the broader stretegic centext.


